

The purpose of this paper is to introduce one more of a class of games which are now becoming commercially viable, namely those games where the computer does not compete but provides the environment for the game and coordinates the players. Himmelbett presents to the players a large choice of tactics based on and simulating closely the actual conditions existing for Bomber Command and the Luftwaffe in 1942.
There are two distinct ways of playing games with computers. The best known is the attempt to program the machine to play a game in competition with a human opponent. In this approach the intent is either to win the game or to simulate and study how humans may possibly make complex decisions.
This approach is now in decline for a number of reasons (see Bell, 1972), the more obvious being lack of commercial interest, the diminishing returns of conventional techniques and the render unto Caesar effect, i.e. the machine's advantages of perfect memory and high speed result in algorithms which are not remotely humanoid. It is also debatable whether chess masters are good models for a realistic study of humans making decisions.
The second approach to game playing is now commercially viable in America. In this case the computer does not compete but provides the environment for the game and co-ordinates the players. Examples are Space War (no reference known) which requires a visual display and complicated controls for the players and Kriegspiel by Wetherell, Buckholtz and Booth (1972).
The purpose of this paper is to introduce a new game which does not require the programming effort of Kriegspiel but, although its running requirements are also much lower than a chess referee, still presents to the players a large choice of tactics based on and simulating closely the actual conditions existent for Bomber Command and the Luftwaffe in 1942. The game is open to further complication for expert players.
In 1940 Bomber Command of the RAF began attacking German targets. As at the time the Germans had no effective night fighter defence, their first reaction was to use ordinary day fighters manned by crews trained in night flying.
At the end of 1940 it became clear that visual sighting of the attackers was ineffective because the bombers would choose moonless nights or nights when there was cloud cover. To overcome the problem the Germans introduced a system of interception controlled by ground radar. A barrier of radar stations, at intervals of twenty miles, was constructed through which the bombers had to pass. Each station had two Wurzburg radar sets which had a range of about thirty miles; one set would track the fighter and the other would track an intruder passing overhead. The ground controller would direct the fighter to a visual contact range (about 500 yards) preferably below and behind the bomber. The system and tactics were given the code name Himmelbett (Four Poster Bed).
The system worked well initially; the controllers were skilful and interceptions were almost certain. Once the fighter had visual contact, the result was usually cold-blooded murder. The British reaction was also cold-blooded but statistically logical. If the bombers flew in a tight stream over one station then many would pass through because the defence could only engage one bomber at a time, each engagement lasting about ten minutes. The German reaction to streaming was two fold: to deepen the barrier and to equip the fighters with on-board radar sets called Lichtenstein, with a range of about two miles. This equipment reduced the time of ground control to a visual contact considerably and allowed a ground controller to handle a number of fighters.
The Himmelbett system was finally rendered obsolete in July 1943 by the use of Window, bundles of aluminium foil strips which, when dropped from a bomber, broke up and produced a radar echo similar to that of a large aircraft. The WurZburgs were blinded but, because of relative velocities, Lichtenstein could still discriminate the bombers.
The Germans again had to evolve their defence. Depending on their Lichtenstein sets, the fighters now tried to locate and enter the bomber stream. If successful they would first report the location and course of the stream and then engage the enemy continuously to, over and from the target. With these tactics it was important to identify the stream and target so as to organise the defence effectively and, conversely, for the attackers to practice deception to hide their true objective.
The computer game described in this paper should recreate the relevance of these wartime lessons. It also emulates some of the aspects of wargaming which the armed forces of many nations study and practice with extremely sophisticated special purpose computers, e.g. partial information of opponent's moves, theory of pursuit and capture. (Isaacs, 1965; Wilson, 1968).
The moves are simple but can easily be extended for skilful players. Detection of the fighters is one possible addition. In actual fact some bombers could detect when they were held in a Wurzburg beam and would then take evasive action also attempting to jam the ground-to-air control of the fighter; the rear and top gunners would also be on the alert knowing that the fighter would try to approach from below and behind which improved their chances of sighting and shooting the fighter down.
For further information on night-fighting tactics see Price, (1969) and Deighton (1970).
The game is played on two boards, Bomber and Fighter, which the computer co-ordinates. Neither player can see his opponent's board. The boards are 9 by 12 grids and the aircraft have a choice of 9 altitudes i.e. the game is three-dimensional.
Any aircraft trying to move out of the game space has its move ignored except if it dives into the ground, in this case theair craft is reported lost.
Fig. 1 is an example of a possible opening position.
Column B of the Bomber's board is his Base. In this column he may place nine bombers in any formation he wishes. He may, in fact, place all his bombers in one cube but this is a bad tactic as will be seen.
To win the Bomber must get at least five of his aircraft over a single square in the TARGET column; altitude does not matter. Note the conventional direction of the target in that all war films show the Allies flying from left to right when attacking Germany. The exception that proves this rule is when Americans attack Japan, for this version of the game the boards must be turned round.
The Bomber does not announce his target square until the end of the game. A move for the Bomber is one cube in any direction for each of his bombers, i.e. six possibilities usually but don't forget a possible null move. The moves are coded Climb, Dive, North, South, East and West.
He may delay takeoff of an individual aircraft indefinitely but once a bomber enters the CHANNEL it has only 16 moves left.
The Fighter's board is slightly restricted. He has two fighters (altitude underlined) which can range over the entire board but initially he must place two 4 by 4 grids anywhere he chooses (they may overlap) to the right of the CHANNEL and the fighters must start within these grids.
The computer will inform the Fighter of the presence of a bomber in the CHANNEL and will reveal completely the nearest bomber within the fighter grids on a 1:1 basis, i.e. if there is only one fighter in the grid then the nearest bomber (or bombers if equidistant) is revealed. This means that if the nearest bomber is sharing a cube then all its companions are revealed.
A Fighter move is four cubes, in any direction and order, for each of his fighters with a bonus of two extra moves if the fighter has just made a kill. For example NSEW would effectively orbit the fighter at a constant altitude if it has no contact.
A bomber is shot down if any of the cubes it enters were occupied or passed through by a fighter on the fighter's previous move. There are usually five such cubes and seven after a kill. Bombers destroyed are reported to both players by the computer.
To win the Fighter must destroy at least five bombers; however, to offset his mobility advantage, each fighter is restricted to a maximum of four kills. Bombers destroyed over the target square do not count as destroyed in time.
The Bomber also has some information about his opponent's moves. He can overhear the previous Fighter's commands after completion of his own move but does not know to which fighter they refer. Because of this the Bomber can sometimes calculate, when he loses a bomber, which of his remaining aircraft will be revealed to the defence and take evasive action.
To illustrate some aspects of the game consider Fig. 2. This is a record of the activity in one of the fighter grids from the computer's point of view. The computer's co-ordinating messages are given in brackets, the fighter's altitude is underlined and the grid is against the top of the board in Fig. 1.
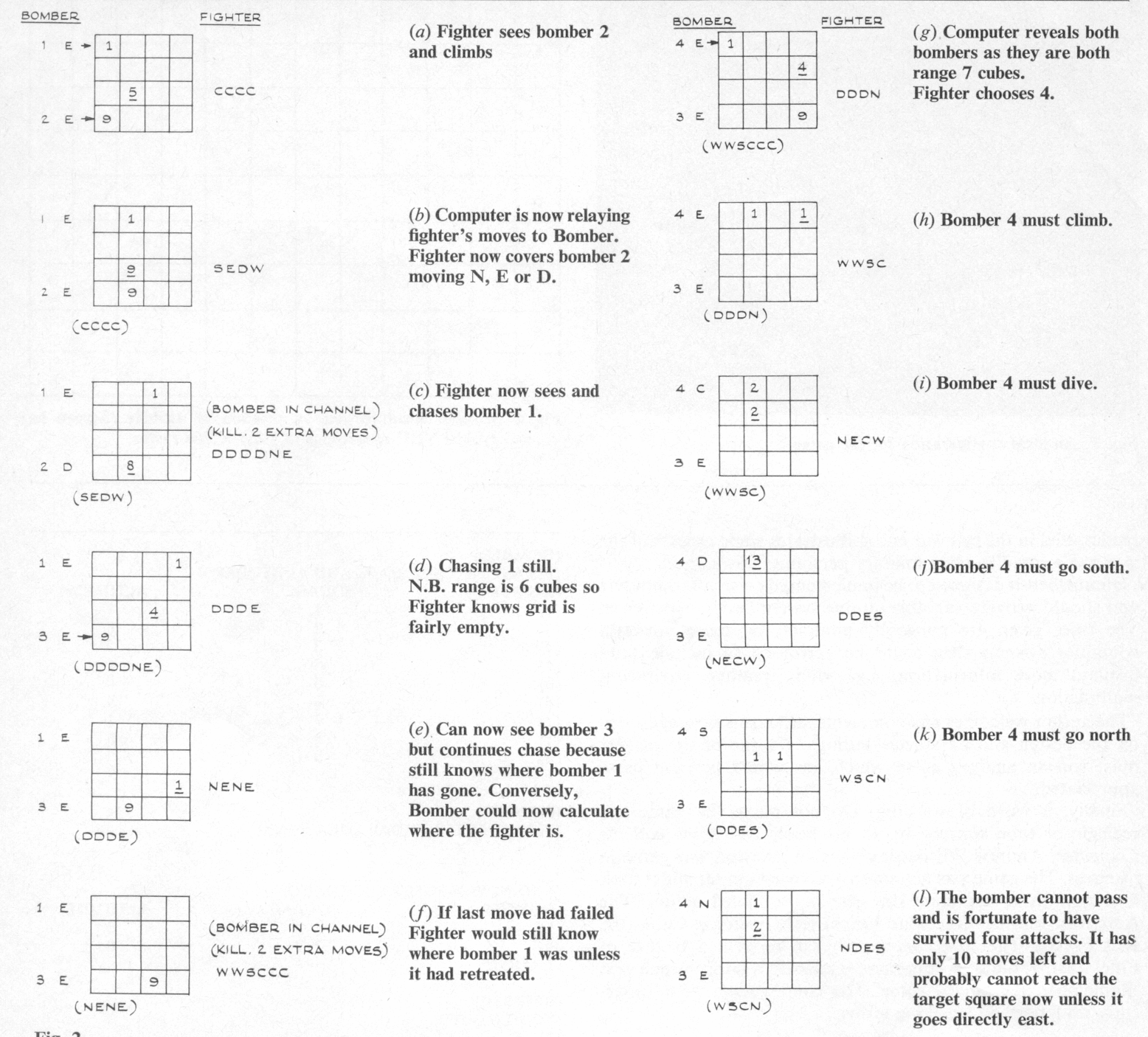
The Bomber's moves are entered first (on the left) and the partial position is then revealed to the Fighter. His response (on the right) is to chase and attempt to pass through a cube the detected bomber is about to enter.
The computer relays the player's moves, checks legality, updates the boards and reports kills to the Fighter and the Bomber.
The Bomber has chosen to spread his aircraft and the fighter has to make long chases. The result is that the fighter can be forced eastwards out of his grid but as the bombers take little evasive action (except bomber 4) the fighter can just handle three intruders.
The Bomber's tactics are, as already stated, to concentrate his attack so as to overwhelm the defence. However deception also plays an important role in his game; streaming all the bombers through one grid will only cause the defence to bring up the other fighter because an empty grid is easily detected. This crowded tactic magnifies the mobility of the defence if they detect and counter it correctly. The Bomber can attempt to find the corridor the grids cannot cover (it must be at the top, middle or bottom of the board) but the Fighter can double-bluff such attempts and still has a powerful defence tactic if he thinks the Bomber has found the blind spot. The tactic covers the corridor completely and still allows the Fighter to check each of his grids for contacts at alternate moves.
Despite the simplicity of the moves it is difficult to play the game with a human co-ordinator because the chance of error is high. The game is best played on a computer with two visual displays. Fig. 3 shows an ideal setup. The screens' dimensions are fortunately in the ratio 9 to 12.

Nevertheless it is recommended that should anyone be interested in implementing the game he should first gain some experience of the players' requirements via hand simulation.
Minimum configuration for the game is a minicomputer with two on-line typewriters.
The first problem is to identify which of their aircraft the Bomber and Fighter wish to move. Fig. 4 is a closeup of the opening position for a Bomber on one of the screens shown in Fig. 3. This shows the feasibility of identifying a bomber by the position of its altitude in the square. In this example the top lefthand corner is bomber 1, the middle of a square identifies bomber 5, etc.
The Fighter's problem is simpler. With only two aircraft he just remembers which fighter is which. He should however have the option of asking the computer to identify a fighter for him and this illustrates an important feature of a good on-line implementation. Such an implementation will have a great deal of prompting from the computer. The players should only ask and answer questions rather than give commands.
For example, to set up the opening position shown in Fig. 1 might be done as in Fig. 5. The simple command language with the computer prompting (again in brackets) is kept short to allow for a slow, mechanical I/O device. A screen display should present more information.
(BOMBER)
(PLEASE ENTER SQUARE AND ALTITUDE)
(NUMBER SQUARE ALTITUDE)
(1) 1 1
(2) 2 5
(3) 3 9
(4) 4 1
(5) 5 5
(6) 6 9
(7) 7 1
(8) 8 5
(9) 9 9
(THANKS)
(FIGHTER)
(PLEASE ENTER RADAR LOCATIONS)
( X Y X Y)
2 2 2 7
(AND NOW FIGHTER LOCATIONS)
(NUMBER SQUARE ALTITUDE)
(1) 2 3 5
(2) 2 7 5
(THANKS)
(BOMBER)
(YOUR MOVE)
(1) E
(2) E
...
(FIGHTER)
(BOMBER IN CHANNEL)
(1) NEWS
(2) NEWS
Fig 5
The game described in this paper is representative of a commercial trend in game playing with computers. On page 46 of Strategy and Tactics, March 1972, there is an advert inviting the reader to pay for the opportunity to play computer controlled war games (one is called Nuclear Destruction). Exactly why the more conventional computer games such as chess, draughts, Gomoku, etc. have not been similarly exploited is difficult say. A possible reason is that the conventional games are of the perfect information type in which skill and experience are important whilst luck has little effect.
These new games emphasise luck; they depend on incomplete (sometimes incorrect) information and possible malfunction. Consequently they require less skill but are more realistic.
The new games are also intended to be educational. In the case of Himmelbett the game should make the players recreate tactics used in the last war and it illustrates some aspects of the war games used to train military personnel nowadays.
Himmelbett is designed to be implemented on small computers and should provide valuable on-line system design experience. The rules given are purposely minimal; on more powerful computer systems they could be expanded to include (and display) more information, e.g. wind, weather, equipment malfunction.
The author welcomes any comments, criticisms or suggestions on the design and parameter settings. As one of the players must win an analysis as to which one would be even more appreciated.
Finally, a word of warning. Do not make the game too realistic or time consuming. In his book The Bomb and the Computer, Andrew Wilson describes an invasion war game in progress. The game was not controlled by computer and it took four months to represent one day of simulated action. The American Marines (the Blue Force) were invading Cuba (the Red Force). The Red commander sat beneath a picture of Fidel Castro; the Blue commander beneath a notice which said Remember, it's only a game. The commanders were apparently no longer on speaking terms.
The author would like to thank officers of the RAF College, Cranwell for some informative discussions.
BELL, A. G. (1972). Games playing with computers, Allen and Unwin, pp. 191-196.
DEIGHTON, L. (1970). Bomber, Jonathan Cape.
ISAACS, R. (1965). Differential games. A mathematical theory with application to warfare and pursuit, control and optimisation, J. Wiley and Sons Inc.
PRICE, A. (1969). Messerschmitt Bf 110 Night Fighter. Profile 207. Profile Publications.
WETHERELL, C. S., BUCKHOLTZ, T. J., and BOOTH, K. S. (1972). A director for Kriegspiel, The Computer Journal, Vol. 15, pp. 66-70.
WILSON, A. (1968). The Bomb and the Computer, Barrie and Rackliff.